Part 3. VPN LAN for OSINT & more
For OSINT and other purposes, I wanted to build a LAN that routes all internet-bound traffic through a VPN. I want to run VMs in said lan (kali, buscador) and also access with physical devices over wifi, like smartphones bought with cash with prepaid SIMs also bought with cash, and configured & accounts set up in a park downtown while drinking beer.
As VPN provider I'm using PIA VPN. Not sure if a VPN provider can ever be trusted, but the same could be argued for any ISP as well. Anyway, PIA is reasonably easy to setup on any device. They also provide instructions on how to configure it on pfSense.
I tried to be clever and configure my physical pfSense installation to only route one LAN via PIA and the rest through my ISP but never quite got it working. My pfSense already had a somewhat complex configuration, so instead of troubleshooting it, I went for a different approach. Now that I'm already running Proxmox in a cluster that has plenty of spare capacity, I installed it on a virtual machine.
VLAN setup
The VPN LAN needs to be reachable by the proxmox server itself, any guests running on it, or any guests running on any other proxmox cluster node, or by the Wifi bridge. Therefore, it needs to be physically accessible (as opposed to only VMs on a single host needing to access it) so I assigned a VLAN to it. I picked an arbitrary VLAN ID 4 to be used here.
First, I modified my switch config to make vlan 4 available to the ports for all proxmox hosts and my wifi AP. Then I configured my wifi AP to bridge vlan 4 to a virtual access point. See part 1 of my lab writeups in case you are interested in how to do that on a MikroTik AP.
pfSense
I created a new VM to run pfSense. Its WAN interface can be bridged to the production LAN. Its LAN interface needs to be tagged with the VLAN ID (4). Like this:
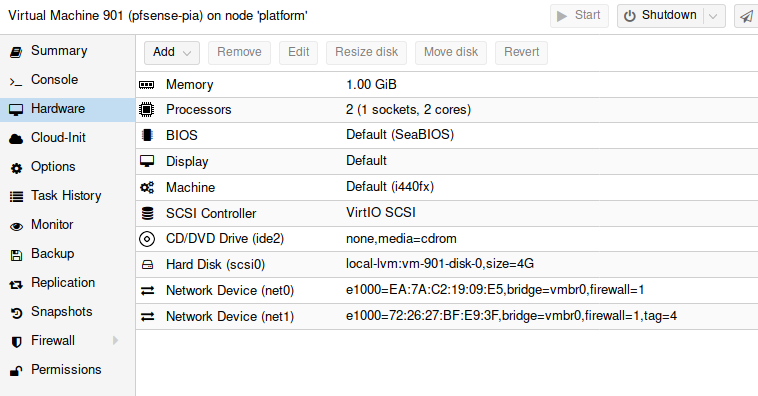
Then I installed pfSense with default settings. For LAN subnet I picked another subnet than used elsewhere in my setup to avoid confusion. Then I followed the instructions to configure PIA. Note that to configure this pfSense installation, you need to access it from its own LAN–either spin up a new VM and put it on the same VLAN, or just connect through the new virtual wifi AP.
To test this, I created a new Debian VM, and configured its ethernet to access the VLAN with tag 4:
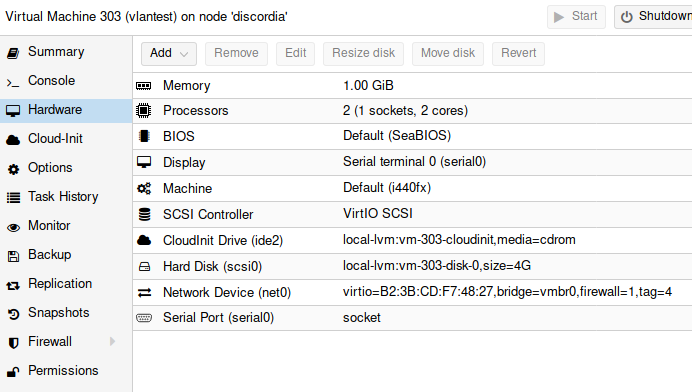
Now, checking the public IP of the new guest:
debian@vlantest:~$ wget -qO- https://ifconfig.co
212.92.104.55
Shodan says it's elsewhere than with my ISP.
Summary
- a special LAN that routes its outbound traffic through a VPN
- physical access to the lan using a VLAN
- virtual machines access the VLAN by using a tagged interface. VMs don't know they are on a VLAN
- Wifi AP bridges the VLAN to a virtual AP